Bash bug on Apple, Linux computers leading to attacks, experts say
- Share via
A program that comes pre-installed on Apple’s Mac and MacBook as well as millions of other computers has a flaw that could let hackers take control of the computer, cybersecurity experts said Thursday.
Hackers would gain access to everything on the computer, such as “sensitive information, confidential information, intellectual property, customer data, financial data – the list goes on – including the ability to make changes,” Kyle Kennedy, chief technology officer at data security firm STEALTHbits Technologies, said in a statement.
The Department of Homeland Security’s computer security team also issued an alert about the bug, which cybersecurity experts said had the highest threat-level rating and required only minimal wits to exploit.
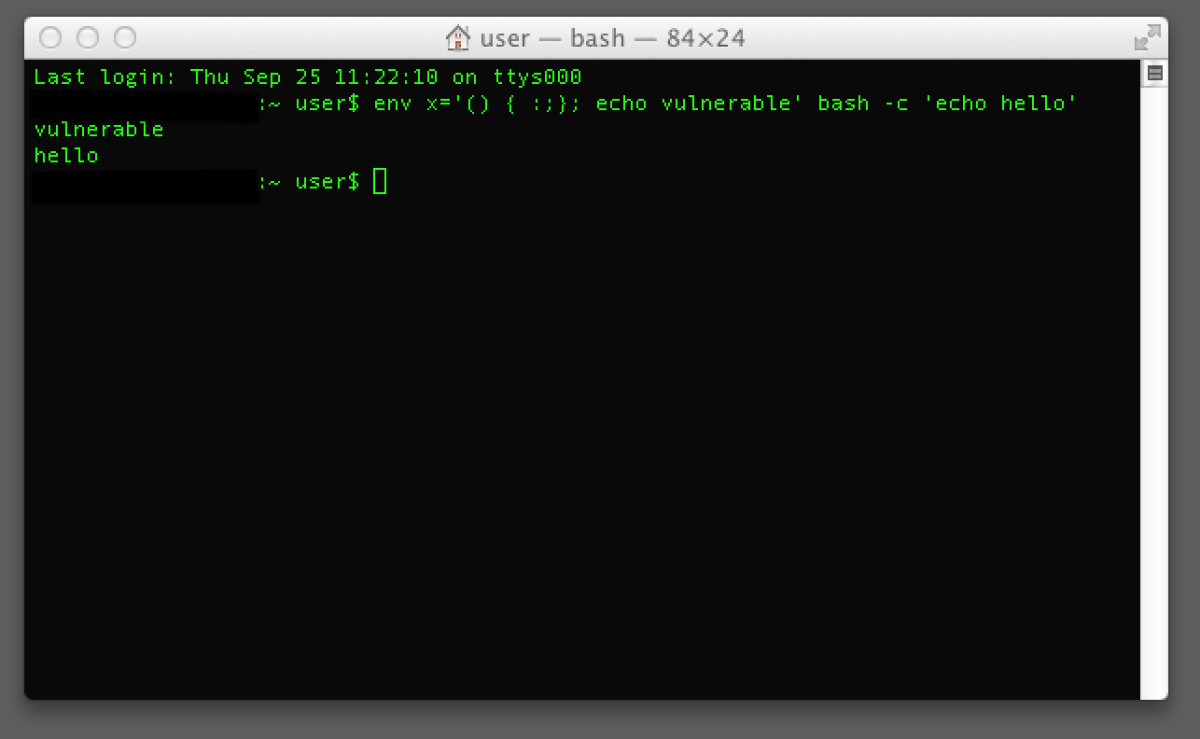
The affected program, Bash, is rarely used by anyone other computer programmers. It allows users to write coded text commands that translate to actions on the computer, from simple things like deleting files to complex tasks like changing network set-ups. But many other pieces of software use Bash in the background, often without the computer user realizing.
Bash is known as a “shell program,” spawning the name “Shellshock” for the bug.
Operating systems based off Linux, including CentOS, Debian, Redhat and Ubuntu, have issued updates to begin squashing the bug, the Department of Homeland Security said. Apple, which develops the OSX operating system, didn’t immediately respond to a request to comment.
Cable boxes, routers and other Internet-connected devices also run Bash, said Chris Stoneff, director of professional services at Lieberman Software. The breadth of devices vulnerable makes the bug a juicy target for hackers, he and others said.
The security firm Bitdefender said it had already seen attacks against Internet servers on Thursday, noting that the threat usually involves an automated program that tries to sneak in a malicious command to the server.
Some experts recommended encrypting sensitive files as a precaution.
Chat with me on Twitter @peard33







